
Pentest Chronicles
Password reset flaw:
when anyone can reset your password

Sebastian Jeż
May 29, 2024
Introduction:
During rigorous testing, security researchers uncovered a significant weakness in the password reset mechanisms used by numerous online platforms. By exploiting the seemingly harmless phone number field, an attacker can compromise a victim's account. The vulnerability lies in the mishandling of a four-digit code, which, instead of being sent solely to the owner's phone, is also included in the server's response. This oversight turns a seemingly harmless feature into a gateway for hackers to infiltrate users' digital lives.
Understanding the Vulnerability
To understand the magnitude of this vulnerability, let's examine how the attack unfolds. Armed with the victim's phone number, an attacker navigates to the password reset functionality and initiates the process. As the four-digit code is generated and sent to the victim's phone, it also finds its way into the server's response. This flaw allows the attacker, through careful manipulation of the communication flow, to intercept and obtain the code. Armed with this critical piece of information, the attacker can seamlessly reset the victim's password, granting them unrestricted access to the compromised account.One of the most alarming aspects of this vulnerability is the minimal effort required for an attacker to gain control over a victim's account. By exploiting the flawed password reset functionality, hackers can bypass traditional security measures, such as two-factor authentication, rendering them ineffective. This significantly lowers the barrier of entry for malicious actors, making unsuspecting users vulnerable to unauthorized access, data breaches, and potential identity theft.
The consequences of falling victim to this vulnerability extend beyond individual users. Organizations relying on online platforms and services to conduct business face a heightened risk of data breaches and compromised accounts. Imagine the impact on an e-commerce platform that falls prey to this attack, with attackers gaining access to customer accounts, personal information, and financial data. The reputational damage and legal repercussions can be severe, further emphasizing the urgency of mitigating such a vulnerability.
Mitigation Strategies Addressing this vulnerability requires concerted efforts from platform providers. Platform developers must prioritize rigorous security testing and implement robust safeguards to ensure the integrity of their password reset functionalities.
Logical flaws in software applications pose a significant threat to cybersecurity, highlighting the need for robust security measures. These flaws often involve missteps or oversights in the logic and functionality of an application, which can be exploited by attackers to gain unauthorized access or manipulate system behavior. Unlike traditional vulnerabilities that rely on technical weaknesses, logical flaws target the inherent design and flow of an application.
To illustrate the vulnerability, here is a simplified example of what the flawed server response might look like:
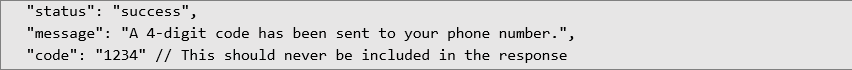
The correct implementation should never include the code in the server's response:
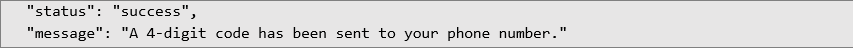
To prevent such vulnerabilities, developers should:
1) Exclude sensitive information: Never include sensitive information like verification codes in server responses.
2) Implement rate limiting: Ensure rate limiting to prevent brute-force attacks.
3) Use secure channels: Send codes via secure, encrypted channels and ensure they are not exposed in any part of the communication process.
4) Conduct regular security Audits: Regularly audit and test password reset functionality to identify and fix logical flaws.
#Cybersecurity #DoSAttack #WebSecurity #Pentesting #InfoSec #PentestChronicles
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


