Pentest Chronicles
Overriding Data Loss Prevention Controls via Misconfigurations and Endpoint Security Bypass

Dominik Antończak
April 17, 2025
Introduction During a recent security audit, however, we identified a misconfiguration within a client’s DLP environment that allowed an auditor to systematically copy data to an unrecognized USB device. Notably, this occurred despite the presence of alerts indicating that such activity should have been prohibited.
This finding revealed serious gaps in the way the DLP mechanisms were deployed and validated. Although the system flagged certain files - namely, those containing IP addresses - it did not consistently block, quarantine, or otherwise prevent the exfiltration of several other files. Furthermore, attempts to transfer docker images and other archived materials were executed successfully, doubting efficacy of the data protection controls in place.
A closer examination of the environment showed that a combination of DLP policy oversights and partial file deletion strategies contributed to the inconsistent nature of the protection mechanisms. In addition, analysis suggested that the DLP solution might be vulnerable to a brute-force which forcefully terminated its processes, disabling any enforcement. This article discusses the root causes, the methods used to confirm the vulnerability, and relevant recommendations to ensure a proper remediation.
Observations from the audit During the initial phase of our audit, we have started from verifying whether the DLP system prevented the unauthorized transfer of sensitive files. The client’s workstation was preloaded with an active DLP agent that restricted copying data to unrecognized USB drives. Testing involved inserting a USB drive not listed in the company’s approved hardware inventory, then attempting to copy various file types onto the device.
The first unusual finding was that while some files were indeed blocked or corrupted (especially those containing patterns matching IP addresses), most other files were transferred successfully. This included documents, compressed archives, and other artifacts that should have been classified as sensitive and restricted. The client’s security team believed the DLP solution would intercept all such attempts, but the logs and real-time notifications showed only some detection events.
Additionally, during deeper analysis, we discovered that the DLP system’s default policy definitions contained partial blocking rules. Only files matching specific known signatures or certain predefined patterns were prioritized for active blocking. Consequently, “neutral” file types or those not explicitly flagged by the signature-based detection process were transferred to the USB device undisturbed. The DLP agent did log certain events internally, but these were not escalated, leading to a false sense of security on the part of the organization.
Another area of concern was the DLP’s inability to handle docker image archives. By utilizing Docker’s native commands (docker save and docker load), the auditor compiled a web application image, stored it in a TAR archive, and easily transferred it to the unapproved USB drive. Even though an error message ( “Operation not allowed”) appeared, the process continued not disturbed, and the file ended up on the USB drive. The DLP system not only failed to stop this transfer, but it also presented misleading feedback to the user, which could be exploited by malicious actors.
Technical analysis and Proof of Concept To provide concrete evidence of the flaw, the following proof of concept was conducted. With basic access to the workstation, the auditor confirmed that Docker was installed and that images were stored locally:
 The auditor proceeded to save a docker image into a TAR file named backup-webapi.tar:
The auditor proceeded to save a docker image into a TAR file named backup-webapi.tar: 
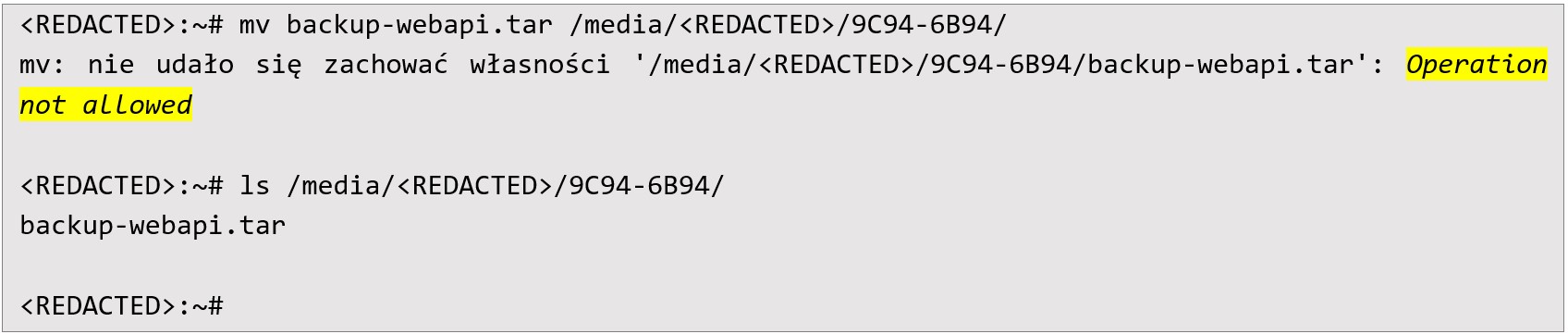
Next, the TAR file was moved to a mounted USB drive located at /media/REDACTED/9C94-6B94/. Despite the console output displaying an error message suggesting the operation was disallowed, the file indeed appeared in the destination directory:
 Upon restoring the file on the auditor’s own system using docker load, it became evident that the TAR archive was fully copied. Additional attempts employing commands like cp and the graphical file explorer further confirmed that no consistent DLP mechanism prevented data exfiltration of this nature.
Upon restoring the file on the auditor’s own system using docker load, it became evident that the TAR archive was fully copied. Additional attempts employing commands like cp and the graphical file explorer further confirmed that no consistent DLP mechanism prevented data exfiltration of this nature. 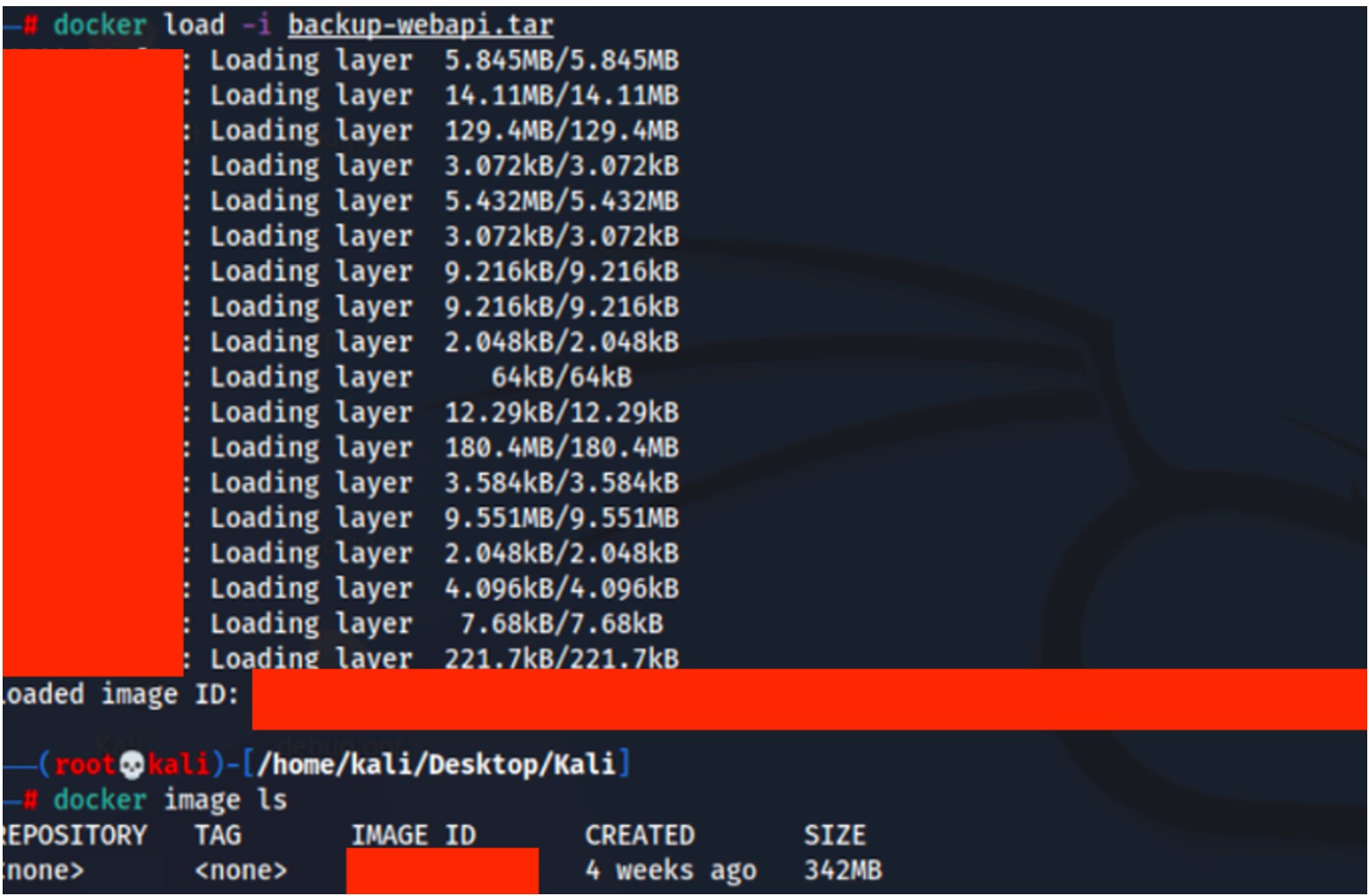
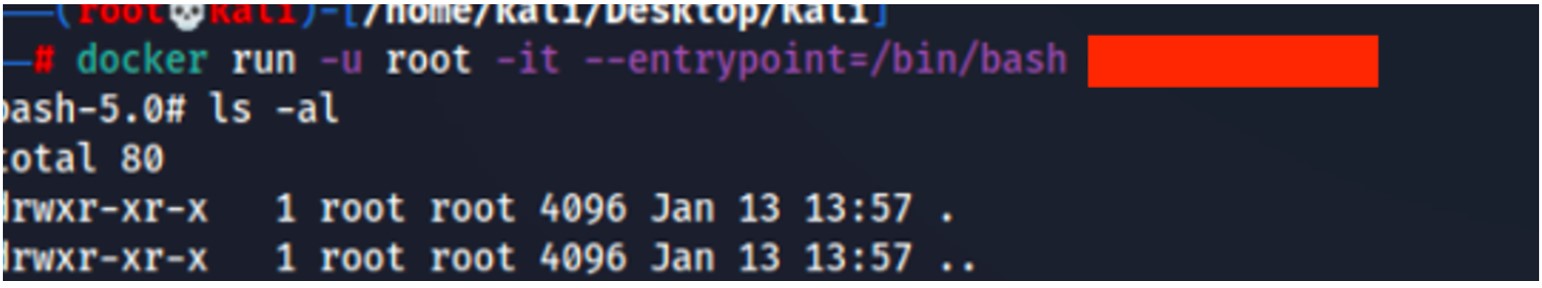 Curiously, the DLP agent sporadically deleted or corrupted certain files, often based on the presence of IP addresses or other patterns in the content. However, those interventions were incomplete and highly unpredictable. Once the docker images and similarly structured archives were not flagged by the signatures or policies in place, they effectively bypassed the DLP mechanism entirely. From a forensic perspective, this partial blocking mechanism can create a misleading environment where an organization believes certain controls are effective, while critical data in alternative formats continues to leak without detection.
Curiously, the DLP agent sporadically deleted or corrupted certain files, often based on the presence of IP addresses or other patterns in the content. However, those interventions were incomplete and highly unpredictable. Once the docker images and similarly structured archives were not flagged by the signatures or policies in place, they effectively bypassed the DLP mechanism entirely. From a forensic perspective, this partial blocking mechanism can create a misleading environment where an organization believes certain controls are effective, while critical data in alternative formats continues to leak without detection. Retest and ESET integration challenges To determine whether subsequent changes addressed the vulnerability, a second retest was performed. The client had integrated an additional layer of security through ESET, which seemingly blocked unknown USB devices by default. Although this system provided some enhanced protection in theory, the auditor discovered a straightforward method to bypass the restrictions.
Using a simple one-liner script, the auditor repeatedly scanned system processes for “ESET” and forcefully terminated them:
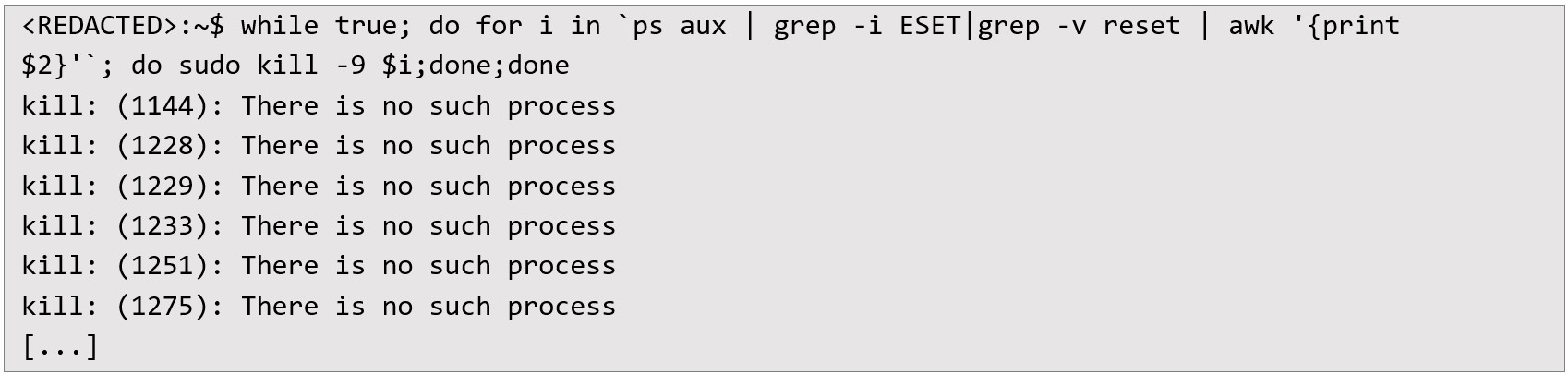 By constantly restarting the kill sequence, the ESET application was effectively prevented from running. As a direct consequence, the attempted blockade of USB devices was disabled, allowing data transfers to proceed without any problems. Moreover, the repeated termination of ESET processes caused near-complete system instability for the security application, rendering it incapable of performing any real-time scanning or device control.
By constantly restarting the kill sequence, the ESET application was effectively prevented from running. As a direct consequence, the attempted blockade of USB devices was disabled, allowing data transfers to proceed without any problems. Moreover, the repeated termination of ESET processes caused near-complete system instability for the security application, rendering it incapable of performing any real-time scanning or device control.  In essence, a mechanism designed to lock down USB ports failed under active interference from a simple script, thereby illustrating that security solutions relying solely on continuous background processes can be defeated with minimal effort if self-defense mechanisms are absent.
In essence, a mechanism designed to lock down USB ports failed under active interference from a simple script, thereby illustrating that security solutions relying solely on continuous background processes can be defeated with minimal effort if self-defense mechanisms are absent. Further analysis suggested that ESET’s self-protection features were not fully engaged, or else they were configured in a manner that did not resist repeated termination attempts. This raised a larger concern: robust self-defense in security tools is critical for preventing exactly this scenario. Without such measures, threat actors with minimal local privileges can eliminate protective services long enough to exfiltrate critical information or execute malicious payloads.
Conclusion
The audit demonstrated that organizational reliance on data loss prevention measures can be misleading when the technology is not properly configured, validated, and reinforced against active tampering. The tested DLP solution exhibited inconsistent behavior, sometimes deleting files based on certain signatures, yet completely ignoring other sensitive archives such as docker images. This vulnerability allows attackers to move valuable data onto external drives without detection. Equally concerning is the ability to disable supplementary defenses like ESET through a simple loop that terminates its processes, an approach that reveals inadequate self-protection capabilities.
Preventing similar vulnerabilities requires a careful review of DLP policies to ensure that all relevant file formats, archiving methods, and exfiltration vectors are covered. Equally important is enhancing endpoint security solutions so that they cannot be bypassed.
Ultimately, organizations should adopt a layered security approach, rather than relying solely on single-point defenses, to ensure that data remains protected under both typical and “hostile” scenarios.
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


