
Pentest Chronicles
Key Insights from Red Team Testing

Krystian Działowy
September 5, 2024
In one of our recent tests of this type, our team, equipped with a wide range of scenarios, successfully infiltrated the client's internal network, gaining access to numerous resources where we obtained credentials to critical assets, such as databases and email accounts.
The capabilities available to the audit team included:
a) On-site attacks
b) Conducting social engineering attacks
c) Reconnaissance and attacks on external infrastructure
d) Attacks within the internal network
Social Engineering Tests (on-site)In the first phase, attention was focused on the physical security of devices exposed within the company’s premises, accessible to outsiders.
In the first phase, attention was focused on the physical security of devices exposed within the company’s premises, accessible to outsiders.
Interestingly, attention was also drawn to the actions of the security guard, who, over the course of an hour, failed to notice the auditor attempting to connect a malicious device to the available ports. The auditor repeatedly left and re-entered the building with new cables and devices, at the end achieving the desired result. Employee Reconnaissance and Preparation for Social Engineering Tests In the case of remote social engineering tests, the first stage involved reconnaissance conducted over the Internet, which revealed potential entry points. Several dozen employees were identified (mainly through social media), along with their email addresses and phone numbers. This data was gathered for the potential execution of further social engineering tests, specifically phishing and vishing.
However, this step was not necessary, as the other part of the team gained access to the internal network through a much simpler method that would have offered potential attackers more opportunities. Network Resource Reconnaissance It turned out that the passive reconnaissance of publicly available resources, allowed the identification of many IP addresses and domains belonging to the client. The auditors focused on one of the hosts that could be identified early on as abandoned - it was an old version of the main portal.
Since the portal had not been maintained for a long time, the auditors quickly found some simple security flaws that impacted the further course of the tests.
Initially, we managed to identify a basic SQL Injection vulnerability:
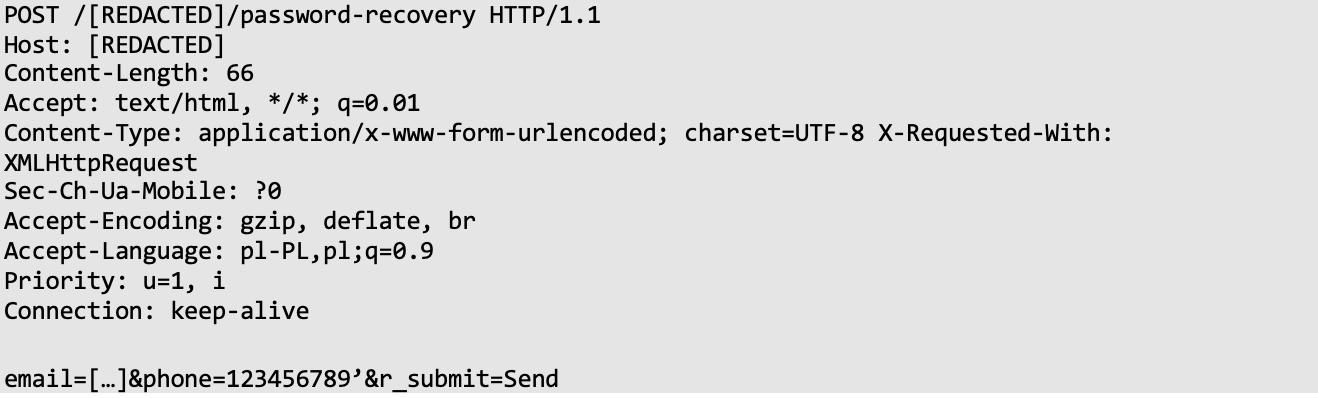 Next, the auditor used SQLmap to retrieve data:
Next, the auditor used SQLmap to retrieve data: 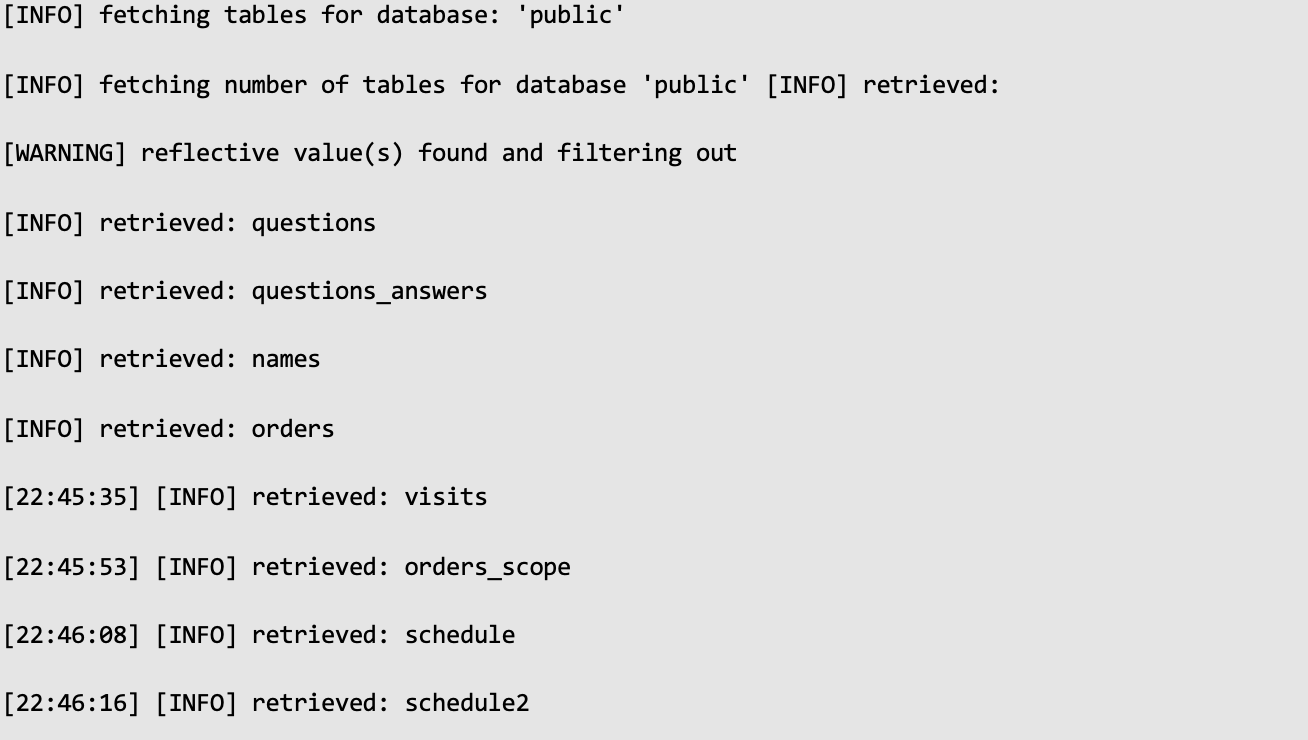 While retrieving the database structures, the auditors continued to examine the application for security issues, which led to the discovery of a Path Traversal vulnerability. This vulnerability exposed the application's source code.
While retrieving the database structures, the auditors continued to examine the application for security issues, which led to the discovery of a Path Traversal vulnerability. This vulnerability exposed the application's source code. Request sent:
 Server response:
Server response: 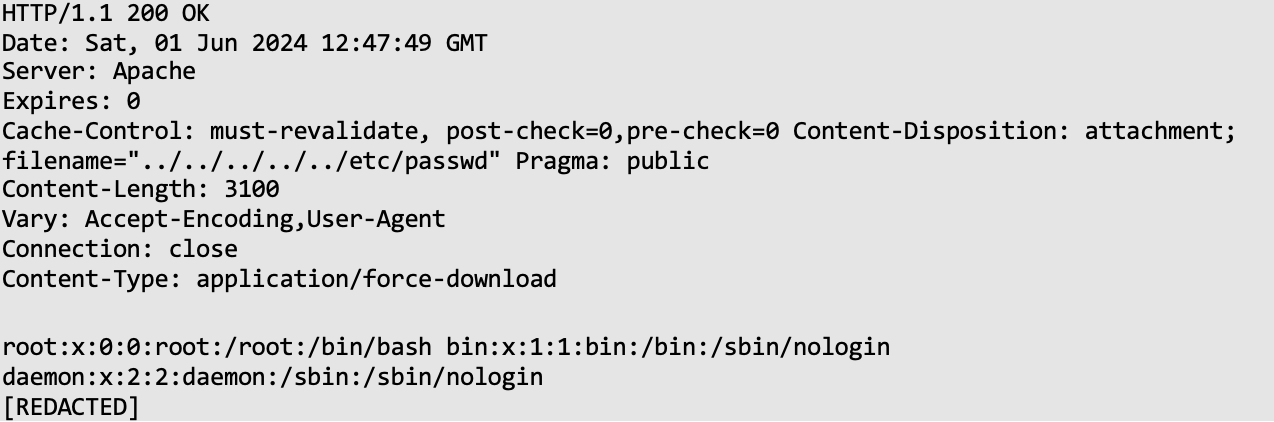 The discovered Path Traversal vulnerability was then used to read the code of the file upload mechanism:
The discovered Path Traversal vulnerability was then used to read the code of the file upload mechanism:  Through a detailed review of the source code, the auditors were able to locate a vulnerability in file upload. The application did not implement proper file type verification, making it possible to upload any PHP script, including a webshell, which is a shell that provides remote access to the web server.
Through a detailed review of the source code, the auditors were able to locate a vulnerability in file upload. The application did not implement proper file type verification, making it possible to upload any PHP script, including a webshell, which is a shell that provides remote access to the web server. Using this webshell, it was possible to execute any PHP command, as well as any system command, with the permissions of the apache account.
Next, the auditors moved on to the active reconnaissance phase of the internal network. To identify open ports among the identified IP addresses, the auditors used the Masscan tool for a quick scan, followed by the Nmap tool to retrieve banners and learn about the services running behind the open ports.
Gaining Access to the LAN and Credentials of Key Systems The information gathered about the software in use, combined with the auditors' knowledge and experience, allowed for the quick identification of critical vulnerabilities. These vulnerabilities led to the security breach, leading to actions such as:
• Gaining insight into the structure of internal databases.
• Obtaining employee credentials for various systems containing sensitive data.
• Gaining access to the main email inbox.
Below is an example of a scan conducted from the level of access the auditors obtained within the LAN network:
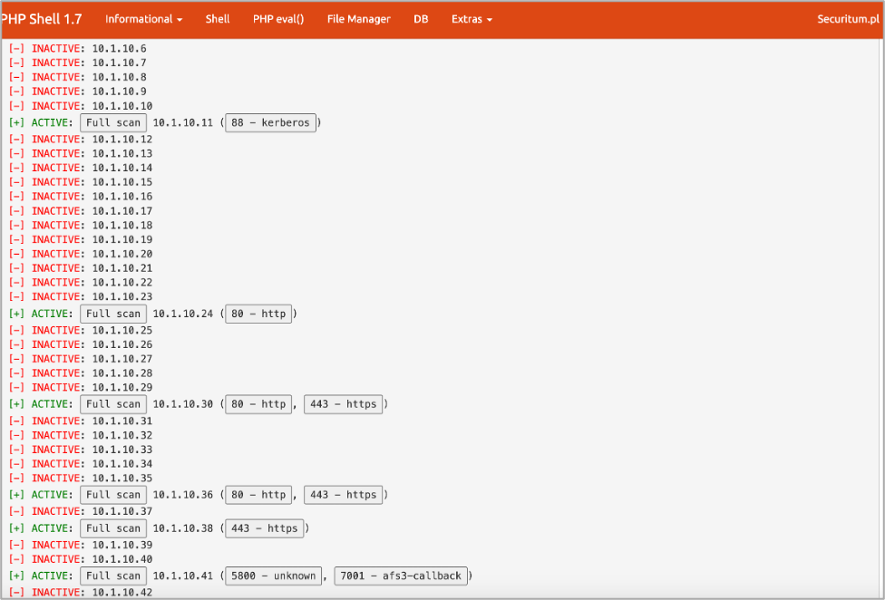 Access to the databases allowed for the potential leakage of sensitive data. It is important to meant that the auditors' activities during the tests were neither detected nor stopped in any way. Therefore, it can be concluded that the test's objective was achieved.
Access to the databases allowed for the potential leakage of sensitive data. It is important to meant that the auditors' activities during the tests were neither detected nor stopped in any way. Therefore, it can be concluded that the test's objective was achieved. Does that seem like a lot? After gaining access to the server, further analysis revealed that it had likely been compromised by cybercriminals several years earlier. In one of the directories, the files "401.php" and "test.php" were found, which contained popular and publicly available PHP webshells.
The client was informed that a thorough analysis should be conducted immediately to determine whether these files ended up on the server as a result of a real attack on the company and whether they were used by potential attackers to extract data from this server.
Summary Based on the Red Team tests conducted, several key conclusions can be drawn:
1. Physical Security is Important: Even the most advanced technological layers can become irrelevant if an organization does not ensure physical security.
2. Problems with Outdated Software: Outdated, and even worse, abandoned systems that are no longer actively used can pose serious threats. Exploiting critical vulnerabilities in an old version of a website allowed auditors to gain access to the internal network and reach sensitive data.
3. The Importance of a Comprehensive Security Approach: The effectiveness of these Red Team tests demonstrated that attackers can use a variety of methods, from physical attacks and social engineering to advanced remote attack techniques. Organizations must adopt a multi-layered approach to security to effectively protect their assets.
4. Monitoring and Incident Response: The fact that auditors could operate within the client’s network without detection highlighted the lack of adequate monitoring and incident response. Even if an attack is successful, it is crucial for the organization to quickly detect it and respond, minimizing the damage.
5. The Need for Regular Audits and Training: Regular security audits are essential for identifying and addressing potential security gaps. Additionally, training employees about threats, especially those related to social engineering, is necessary to effectively defend the organization against phishing and vishing attacks.
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


