
Pentest Chronicles
How NOT to store data in a desktop application?

Mateusz Lewczak
August 7, 2024
Unencrypted configuration files One of the simplest vulnerabilities in desktop applications is the presence of unencrypted configuration files. These files are often located in the same directory as the application's executables, but they can also be placed in system directories like AppData or ProgramData. These files may contain configuration details, logs, and other important information.
A practical way to find these configuration files is using the Procmon tool from the Sysinternals Suite. With this tool, you can set up filters to monitor which files the application accesses, providing a clear path to uncovering potentially sensitive data:
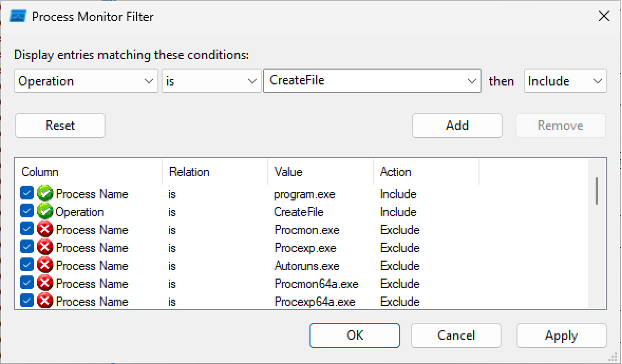
The CreateFile operation is used to obtain a handle to a file, which helps us determine which files an application has opened. Identifying these files can lead to uncovering a valuable information. For instance, during a penetration test, you might find credentials for an email account that the application uses to send notifications. These accounts, often called "no-reply" accounts, are used for sending notifications, such as password reset tokens or temporary passwords.
The impact of this kind of vulnerability can be serious. For instance, if an attacker gains access to a temporary password, they could wait until the user logs in and then hijack the account to set a permanent password. Similarly, if an attacker obtains password reset tokens along with the associated user's email address, they could potentially take over the account. Encrypted configuration files Even when configuration files are encrypted, it's crucial to remember that the application itself must know how to decrypt them. It means that there must be some mechanism within the application that can be reverse engineered to access the encryption algorithm or the key. Sometimes, it is enough to just copy the decompiled code or use an exported function from a DLL file to decrypt the data. Here are a few scenarios that illustrate potential vulnerabilities even when data is encrypted.
Scenario 1: Intercepting sensitive credentialsConsider an application that stores sensitive credentials, like a username and password for an external SMS service, in configuration file that is encrypted. In this case, both the username and password are encrypted. However, the URL pointing to the service is stored in plaintext or can be easily modified. An attacker could change the URL to point the data to a server they control. When the application decrypts the credentials and tries to authenticate with the SMS service, it accidentally sends these plain-text credentials to the attacker's server.
With the credentials to the SMS service, an attacker can cause significant financial loss, impersonate a customer or carry out a phishing campaign. This technique exploits the fact that while the data is encrypted at rest, it must be decrypted at some point for use, creating an opportunity for interception. Scenario 2: Database credentials exposureAnother common scenario involves encrypted credentials to a database. Suppose the configuration file contains an encrypted username and password for accessing the database. An attacker could place a breakpoint at the function responsible for establishing the database connection. By doing this, they can inspect the stack and memory during runtime, where the decrypted credentials will likely be present.
In this situation, no matter how strong the encryption is, once the data is decrypted for use, it becomes vulnerable to exposure. Obtaining database credentials can have severe consequences, such as unauthorized data access, data manipulation, privilege escalation, and further network attacks. In the case of databases like MSSQL and Oracle, attackers can execute arbitrary code, potentially gaining full control over the server.
Additionally, Denial of Service (DoS) attacks may be launched, to disrupt system operations and prevent legitimate user access.
To carry out these attacks, an attacker could use existing tools designed for debugging and monitoring applications. These tools can automate the process of intercepting and extracting sensitive information during runtime. For example, tools like Frida or OllyDbg can be used to inject scripts or monitor function calls, making it easier to identify and extract decrypted credentials or other sensitive information. Treating desktops as back-end components A common practice among developers is to treat desktop applications as the backend of a system. This means that the desktop app is responsible for managing direct database connections, handling user authentication, and communicating with external services. For instance, a desktop app might directly connect to a database to fetch or update user data, like how a backend server would operate. Additionally, these apps might have functionalities to send SMS or email notifications for user verification, password resets, or general communication.
While this approach is convenient, it carries its own set of risks. Like traditional backend systems, sensitive operations handled by desktop applications need to be secured. However, because desktop applications run on the user's machine, they are more vulnerable to reverse engineering and tampering. This exposure can lead to potential security breaches if the application is not properly secured.
Summary In 2024, using desktop applications as backend systems is becoming more problematic and risky. Unlike traditional backends, desktop applications run on users' machines, making them more susceptible to reverse engineering and tampering. Storing sensitive data, like database credentials or API keys, within these applications, even if encrypted does not guarantee security, as the decryption mechanisms can be compromised. Encryption alone isn't enough, as decrypted data can be intercepted during runtime.
To reduce these risks, developers should avoid assigning critical backend tasks to desktop applications. Instead, sensitive operations should be managed by dedicated backend servers, where security measures can be more effectively enforced and monitored. By rethinking the architecture and reducing the exposure of sensitive information, organizations can better protect their systems and data from potential attacks.
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


