
Pentest Chronicles
Heartbleed Vulnerability in 2024:
A Fresh Case from Our Pentest

Paweł Różański
September 20, 2024
What is the Heartbleed Bug?
The Heartbleed Bug is a well-known vulnerability that was first revealed in 2014. It allows attackers to exploit a flaw in OpenSSL’s heartbeat functionality, enabling them to read random portions of the system’s memory. This can result in the exposure of sensitive data such as encryption keys, usernames, passwords, and other confidential information that resides in memory.
To learn more about the Heartbleed Bug, visit dedicated website:
https://heartbleed.com
Real-World Exploitation: What We Found
This case demonstrates the importance of using multiple TLS/SSL tools during testing. While SSLScan did not detect this vulnerability, testssl.sh successfully identified it:
 During our testing, it was confirmed that an attacker could successfully retrieve sensitive information from the affected servers. Using the Metasploit openssl_heartbleed module, we exploited the vulnerability and extracted data from the systems.
During our testing, it was confirmed that an attacker could successfully retrieve sensitive information from the affected servers. Using the Metasploit openssl_heartbleed module, we exploited the vulnerability and extracted data from the systems. In this instance, we managed to obtain credentials for a technical user which were being used for Basic Authentication. The extracted data, encoded in base64, was decoded to reveal the credentials.
 Using these credentials, we were able to bypass the Basic Authentication on the affected host and gain access to the system, as demonstrated below:
Using these credentials, we were able to bypass the Basic Authentication on the affected host and gain access to the system, as demonstrated below: Without Correct Credentials Request:

Response:
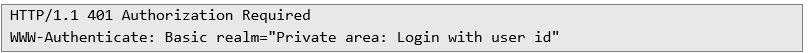 With the Obtained Credentials:
With the Obtained Credentials:Request:

Response:
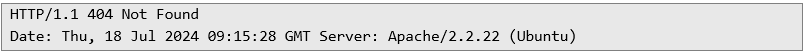
Though the endpoint returned a "404 Not Found" error, the successful authentication process proved that the compromised credentials were valid and could have been used to access sensitive areas of the system had they existed.
Recommendations to Mitigate the Risk
To defend against this vulnerability, we strongly recommend the following:
1. Update OpenSSL to the latest patched version that addresses the Heartbleed Bug.
2. Rotate all sensitive credentials and certificates on the affected systems, as they may have been compromised during the exposure.
#CyberSecurity #DoS #Pentesting #VulnerabilityResearch #ServerSecurity #Infosec #SecurityTesting #PentestChronicles
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


