Pentest Chronicles
From temporary solutions to insecure security practices.

Adam Borczyk
February 06, 2025
Conditional Access feature of Microsoft’s Entra ID allows detailed customization of access policies. Separate rules can be enforced for different groups of users, sign ins can be allowed only from a given location, only on certain device types, certain Microsoft apps and so on.
During one of the recent audits, this checkup revealed an unusual situation – a personal account that belongs to a CEO of the tested company was explicitly excluded from MFA enforcement for mobile devices:
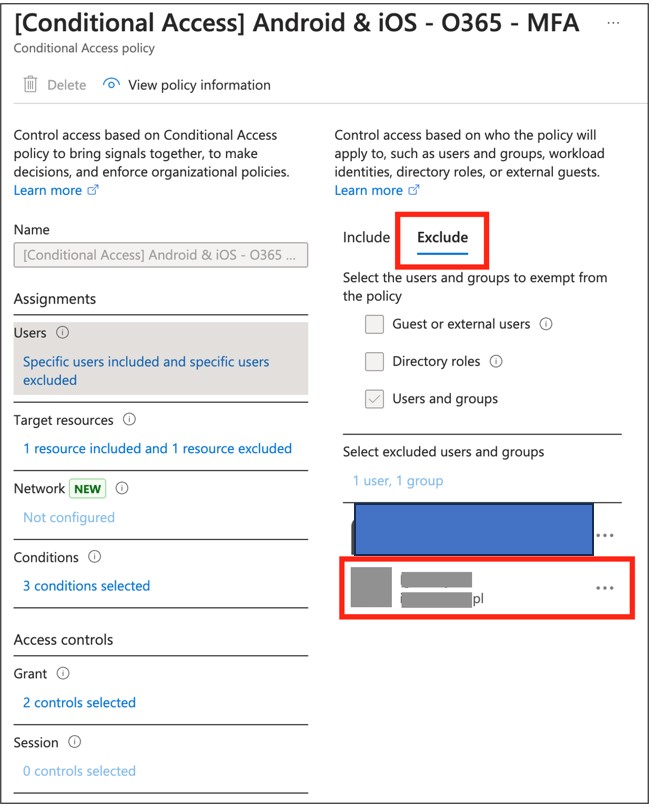 This situation raises an alarm on how the company manages its risks. Further checks of this specific account bring us to sign-in logs panel. Here we can see a list of recent interactive and non-interactive logins:
This situation raises an alarm on how the company manages its risks. Further checks of this specific account bring us to sign-in logs panel. Here we can see a list of recent interactive and non-interactive logins: 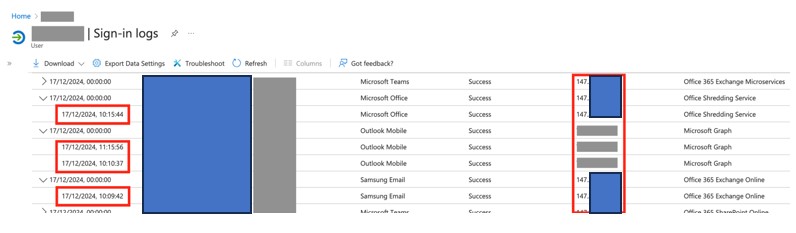 An interactive login is one that requires user’s login and password, to exchange them for access tokens. A non-interactive login in turn, is based on an existing refresh token – password authentication has already been done, now expired tokens are only replaced for the new ones.
An interactive login is one that requires user’s login and password, to exchange them for access tokens. A non-interactive login in turn, is based on an existing refresh token – password authentication has already been done, now expired tokens are only replaced for the new ones. In the screenshot above we a fragment of sign-in logs that shows an unusual activity related to CEO’s account. IP addresses on the right-hand side are located in United States, except for the three grayed-out. These are owned by the company being audited and located in their headquarters in Poland. On the left-hand side are UTC timestamps. Within a minute, around 10 AM, activity from both United States and Poland is recorded, in different services – e-mail client, MS Teams and MS Office. There is a chance some of these log entries could be related to cloud services running on behalf of a user. However, what’s not shown in this screenshot that we had to censor a bit, are more log entries – within the same date, in a span of several hours, there were also logins from IP addresses coming from polish mobile telecom provider and… China. As this indicated a possibility that the CEO’s account has been compromised, the client was promptly notified about the issue, with details in the report.
We, as a company that strives to improve our clients’ security posture, always recommend enforcing MFA for every user account with no exceptions.
In fact, we need to remember that there is a specific spear-phishing variant called “whaling”, when cyber criminals target people who have access to the most sensitive data, such as C-level executives. In that case lack of MFA could lead to takeover of CEO’s account.
If a targeted user account is taken over, it can be used in an attack called Business E-mail Compromise (BEC). Here attackers impersonate the executive, instructing employees or stakeholders to perform some (seemingly authorized) actions, most often related to bank transfers to external accounts.
While MFA is just one of the security precautions that hinders cyber-criminals’ offences and not a silver bullet for every problem, in today’s threat landscape it should be treated as an essential requirement. Loosening standards for certain individuals trades a valuable security mechanism with disputable sense of short-term comfort.
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


