Pentest Chronicles
Exploiting the Password Reset Vulnerability: A Real-World Case Study.

Securitum
December 6, 2024
The flaw in password reset The issue came from the way the application managed password reset tokens. Normally, when a user asks to reset their password, the system creates a unique token specifically for that user to complete the reset process. However, in this case, the application worked differently. By tweaking the request that checks the token, it was possible to trick the system into providing a token for a random user instead of the one making the request. This flaw allowed attackers to take full control of accounts, including those with administrative privileges.
Exploitation time The exploitation process was simple and could be replicated with minimal effort:
1. Obtaining Session Identifiers: First, the attacker navigated to the application and acquired the session cookie (PHPSESSID) and the X-Xsrf-Token header. These identifiers are necessary for sending authenticated requests.
2. Sending a Malicious Request: A crafted POST request was sent to the application’s token verification endpoint. Instead of providing a legitimate token value, the payload contained the parameter "token":{"":null}. This unexpected input triggered the server to respond with a token belonging to a random user.
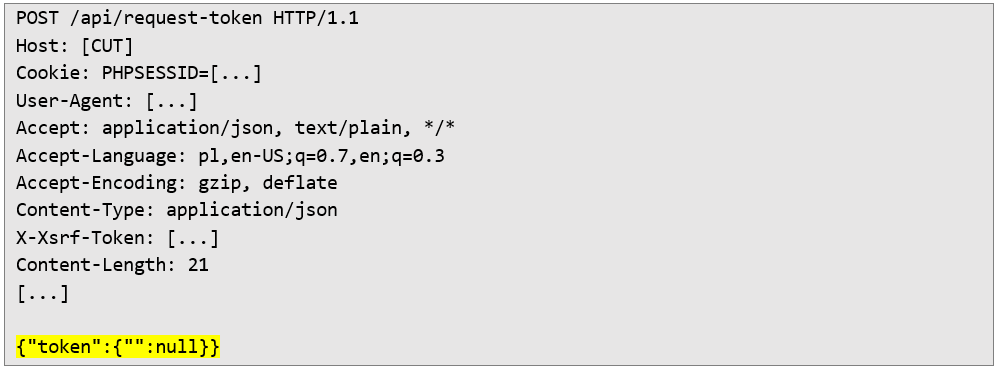 This unexpected input triggered the server to respond with a token belonging to a random user:
This unexpected input triggered the server to respond with a token belonging to a random user: 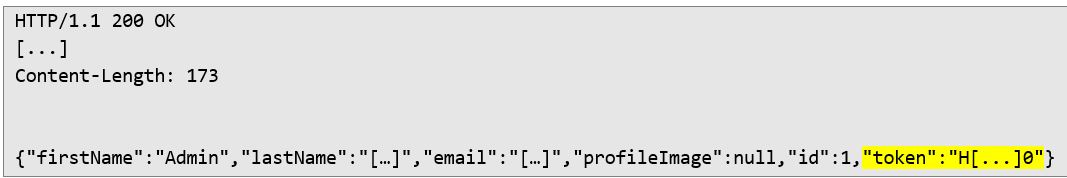 3. Extracting Tokens: Each time the malicious request was sent, the server returned a different token. Using these tokens, the attacker could reset the passwords of multiple users, gaining access to their accounts.
3. Extracting Tokens: Each time the malicious request was sent, the server returned a different token. Using these tokens, the attacker could reset the passwords of multiple users, gaining access to their accounts.  4. Taking Over Accounts: With a valid token, the attacker navigated to the reset password URL, entered a new password, and confirmed the action. This granted them full access to the compromised account.
4. Taking Over Accounts: With a valid token, the attacker navigated to the reset password URL, entered a new password, and confirmed the action. This granted them full access to the compromised account. 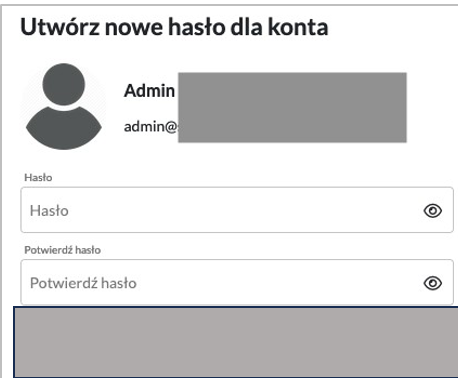 The scope This vulnerability had serious impact:
The scope This vulnerability had serious impact: What went wrong? This vulnerability happened because the application didn’t handle password reset tokens properly. Instead of creating tokens only when someone asked to reset their password, the app generated and stored them in advance, which made it easier for attackers to exploit. On top of that, users weren’t notified when their password reset tokens were used, so attackers could take over accounts without anyone noticing.
The Fix To address this issue, developers should revise how the application handles password reset requests. According to best practices outlined by OWASP, password reset tokens should:
1. Be generated dynamically and only when a reset request is made for a specific user or email address.
2. Be associated with a short expiration period to limit their lifespan.
3. Trigger user notifications whenever a reset is initiated, providing an additional layer of security.
These steps would ensure that tokens are both secure and limited in scope, reducing the risk of unauthorized account access.
Lessons for SDLC This case serves as a reminder that even routine functionality like password resets can become a significant security liability if not implemented correctly. Developers must adopt secure coding practices and test their applications for vulnerabilities.
#Cybersecurity #AppSec #VulnerabilityManagement #SecureDevelopment
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


