Pentest Chronicles
Accessing Internal Network by WiFi Hacking - 2024 Pentest Case

Aleksander Wojdyła
October 25, 2024
Introduction During the last penetration test, I performed an Evil Twin attack, which involves setting up a fake access point with the same name as the legitimate one.
Due to improper configuration of endpoint devices (e.g., computers, phones, tablets), users could accept an incorrect (fake, generated by the auditor) certificate identifying the network. This led to a successful capture of the authentication segment of the communication. Subsequently, the auditor subjected the captured data to brute-force attacks, resulting in the retrieval of credentials.
The captured credentials are domain credentials, meaning several systems rely on a central authentication system (most likely Active Directory), which could enable an attacker to conduct further attacks.
Following network reconnaissance, it was established that the two networks are WPA/WPA-2 Enterprise networks, which require a device certificate, as well as a username and password, for authentication. Wi-Fi clients, however, have the option to either follow the authentication method proposed by the access point or select their own. The standard configuration for Windows, macOS, Linux, Android, and iOS allows bypassing the certificate section and directly entering the username and password.
In the subsequent step, users receive a notification about an untrusted certificate (similar to the HTTPS Man-in-the-Middle attack scenario), and it is up to the user to decide whether to transmit credentials over an insecure channel. Best practices indicate that it is safest when users cannot accept a fake certificate, as described in the following section.
The attack The attack was conducted using the eaphammer tool: https://github.com/s0lst1c3/eaphammer
The first step involved generating a certificate (a fake certificate was generated containing the phrases "COMPANY_NAME" and "COMPANYNAMECA" to build trust). The next step is to activate the tool and start listening:
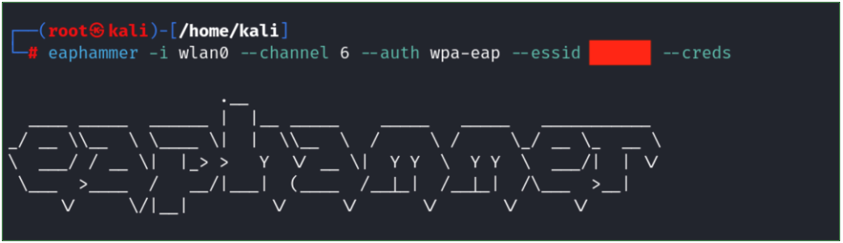 The first result appeared almost immediately:
The first result appeared almost immediately:  After cracking harvesting credentials, password was obtained in hash.
After cracking harvesting credentials, password was obtained in hash. This was next cracked, with the hashcat tool. https://hashcat.net/hashcat/
The auditor was unable to verify whether these credentials were valid (the cracking process completed a day after the audit), however, the mere possibility of capturing such credentials necessitates rating the severity of this vulnerability as CRITICAL.
In this case malicious actors can then access internal network and perform further attacks.
Recommendation It is recommended to implement changes on endpoint devices (phones, computers, tablets, etc.), enforcing network connections only if the network presents a valid certificate (i.e., issued by an internal CA) with a clearly defined Common Name (CN). If devices are managed through an MDM solution, this will be the optimal place to enforce such changes.
#CyberSecurity #PentestChronicles #RedTeam #Infosec #DataSecurity #PenetrationTesting #VulnerabilityAssessment
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


