
Insights
Hacking the invisible: A deep dive into Sub-GHz communication and flaws in the devices we use every day
Mateusz Kowalczyk
December 08, 2023
In our modern world, remote control technology is an ever-present part of daily life. This includes everything from the key fobs in our pockets to the remote controls on our coffee tables. But what lies behind the magic of these devices? In this article, we delve into the world of Sub-GHz communication, a technology in remote control systems, particularly those used for controlling entrance gates or garage doors
At its heart, Sub-GHz communication operates on radio signals, which are essentially electromagnetic waves. The term "Sub-GHz" itself comes from the frequency range it operates in; for remote control fobs, this range extends from 315 MHz to 928 MHz. This makes it clear that the operating frequency is below 1000 MHz, which explains the name Sub-GHz.
The key fob, acting as a transmitter, sends out a signal that the receiver picks up. This receiver then controls the connected device, be it an entrance gate or a car. This brings us to an intriguing question. Given that these gates and cars are often weak spots of our homes and possessions, which we can assume as quite valuable, how secure is this technology? Can we rely on Sub-GHz communication to protect our most precious assets?

Source: https://unsplash.com/photos/a-garage-door-lit-up-at-night-in-the-snow-K_av6e3YnDo
In the quest to make remote control technology safe, one solution stands out - the rolling code. This addresses a critical vulnerability which is the risk of signal duplication, the rolling code ensures that each time you press your key fob, a unique signal for communication is generated. This is crucial in defending against what's known as a replay attack.
A replay attack is an attack method where an intercepted signal is used maliciously. Imagine someone capturing the signal from your key fob and then using it to gain unauthorized access to your car or open your gate. In cases where the signal is the same every time, it is easy to perform, but here rolling code acts as a dynamic shield against such threats.
Diving deeper, we find that rolling code technology isn't just a single type thing. There are various implementations, with KeeLoq being notably popular among key fob manufacturers. KeeLoq, with its origins rooted in the 1980s, is more than just a security protocol; it functions using a non-linear feedback shift register, a concept that might sound complex but is fundamental to its robust security. What we need to know at this moment is that this method ensures that the codes used in remote controls are not only diverse but also incredibly difficult to replicate or intercept.
Further enhancing its security details, KeeLoq has three distinct implementations. Each of these iterations builds on the core principle of KeeLoq, offering varying layers of protection.
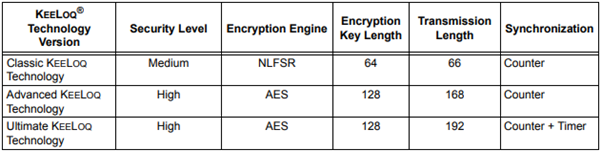
Source: https://ww1.microchip.com/downloads/en/AppNotes/00001683A.pdf
To bring it all together, remote controls are an integral part of our daily lives, quietly ensuring the security of our cars, gates, and other devices. They operate on radio waves, with each iteration bringing new advancements in security. KeeLoq and its multiple implementations stand as testaments to the continuous evolution of this technology. However, this leads us to ask a critical question: despite these advanced security features, can we truly consider our remote-controlled devices as secure?
Legal Disclaimer: All tests and demonstrations in this article were conducted on devices with proper authorization.
To show the nature of radio signals and their functioning, having the right tools is essential. Devices like Flipper Zero or HackRF are ideal for this purpose. In my research, I used the Flipper Zero, a very versatile and useful tool.

The first step in using it is to select the appropriate module from its interface:

With the theoretical knowledge that radio signals operate on various frequencies, the next logical step is to determine the frequency of the device being tested:

Flipper Zero provides two primary modes for reading radio signals:
1. Fixed scan - automatically decodes key from signal.
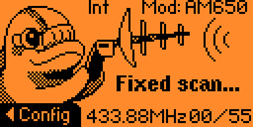
2. Raw scan - creates a file for later analysis or replay.
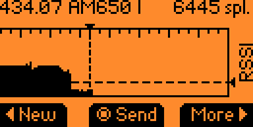
Regardless of the chosen scan mode, it's possible to extract the key from the signal:
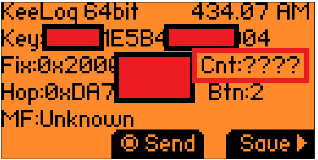
Is that a success? As seen in the displayed results, the key is not only variable; there is the counter value that isn't calculated. This means that, even if someone tries a replay attack, they can't successfully copy the key fob signal to make a working clone. It worked as it should, attackers shouldn't be able to reuse signals due to the rolling code and correct implementation of KeeLoq.
But reality often differs. Many manufacturers rely on the same methods to generate rolling codes, often using a manufacturer key or a combination of this key and a part of the key fob's serial number. Only a few manufacturers use unpredictable seeds for generating codes, which is more secure and makes reverse engineering harder.
My research from this article was proven through tests on three popular key fobs.

Interestingly, using special firmware for Flipper Zero, known as 'Flipper Unleashed,' it becomes possible to decode even the counter (Cnt) for many key fobs from various manufacturers.
Source: https://user-images.githubusercontent.com/10697207/186202043-26947e28-b1cc-459a-8f20-ffcc7fc0c71c.png
After installing the 'Unleashed firmware’, the Flipper Zero was able to estimate the counter and effectively clone the key fob, presenting a potential tool for malicious actors:
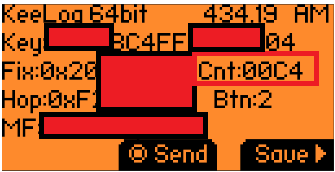
What exactly happened here? The Unleashed firmware performed a brute-force attack, exploiting the fact that manufacturers often use similar or easy-to-guess keys. This approach works instantly.
Considering this research, one might wonder about its impact on our daily lives. With a device costing about $250 and the installation of free firmware, it becomes possible to open automatic garage doors, gates, and barriers. This ‘vulnerability’ exists primarily because suppliers of automation devices haven’t placed enough emphasis on the security of the keys used.
To sum up, despite its age and known vulnerabilities, KeeLoq remains a fairly robust cipher, especially in its enhanced versions. However, the insecurity in radio signals using KeeLoq primarily arises from three issues:
- Manufacturers uses the worst cipher algorithm implementation,
- Manufacturers use static seed to generate rolling code, what is easy to reverse by devices available on market,
- There are many bad implementations on radio transmitters and receivers as well.
#CyberSecurity #TechInsights #SubGHz #Communication #SmartHomeSecurity
Other Insights

Helping secure DOMPurify
MICHAŁ BENTKOWSKI
December 21, 2020
Within last year I shared a a few writeups of my bypasses of HTML sanitizers, including: > Write-up of DOMPurify 2.0.0 bypass using mutation XSS > Mutation XSS via namespace confusion – DOMPurify < 2.0.17 bypass While breaking sanitizers is fun and I thoroughly enjoy doing it, I reached a point where I began to think whether I can contribute even more and propose a fix that will kill an entire class of bypasses.

Pyscript - or rather Python in your browser + what can be done with it
Michał Bentkowski
September 10, 2022
A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in the browser is not new; the pyodide project has allowed this for a long time...

Art of bug bounty a way from JS file analysis to XSS
jAKUB żOCZEK
July 1, 2020
Summary: During my research on other bug bounty program I've found Cross-Site Scripting vulnerability in cmp3p.js file, which allows attacker to execute arbitrary javascript code in context of domain that include mentioned script. Below you can find the way of finding bug bounty vulnerabilities from the beginning to the ...


