Pentest Chronicles
Exploring DaaS Security - part 2: Other available applications on the machine (3rd party)

Mateusz Lewczak
April 12, 2024
When dealing with applications used by regular company employees, often involved in paperwork, it's likely that cloud environments will also include office applications, image viewers, and possibly File Explorer. While these are not hacking tools, they can still be utilized in ways that facilitate access to the system's shell.
Office application
Modern office applications such as Word, Excel, etc., or their alternatives in the LibreOffice or OpenOffice suites, support macros. Macros are code fragments that are used, among other things, to automate certain actions within documents and are an extension of the program's capabilities. As an attacker, we can use this opportunity to run code that will open the command line for us.
Below is an example of how to perform such an attack:
1. Upload DOCX file to Citrix environment.
2. Go to attached files (e.g. User Management module).

3. Create new attachment and upload DOCX image.
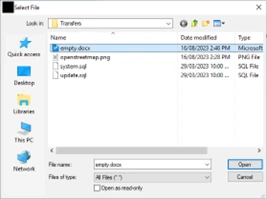
4. Double click newly created attachment, after that LibreOffice will open that document:

5. Select “Tools” > “Macros” > “Edit Macros”, macro manager will open:

6. Select “Tools” > “Organize Macros” > “Basic...”:

7. Chose “empty.docx” > “Standard”, click “New” and then click “Ok”:
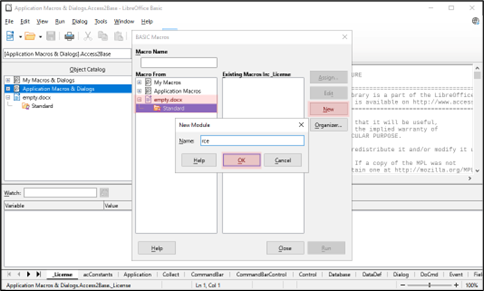
8. Now a new Macro has been created for the opened document. Enter the following content for this file:


9. Now you need to compile this file:
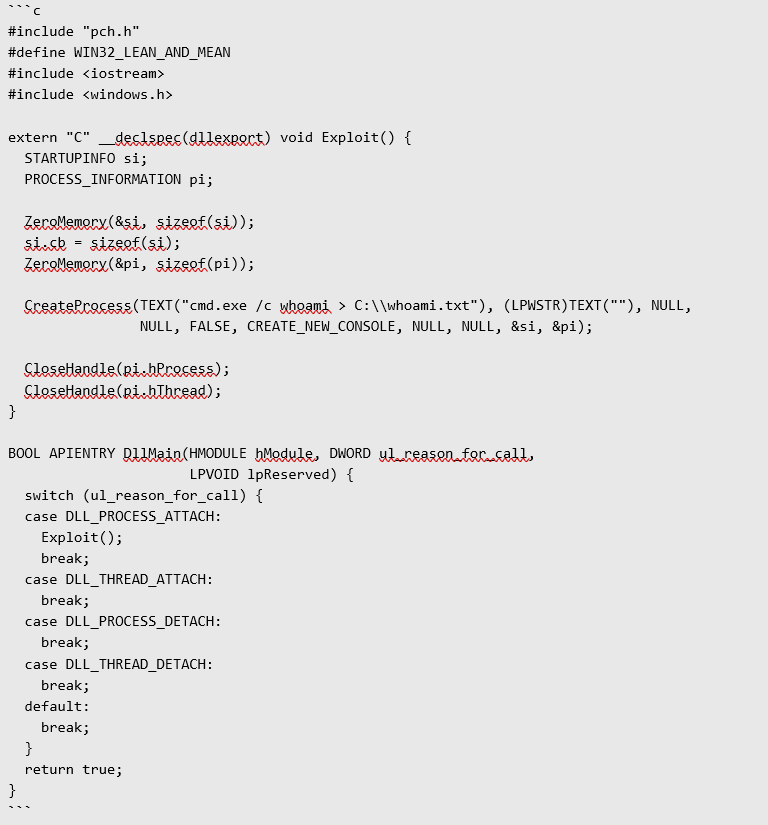
10. Run it:

11. After performing the above actions, a window with PowerShell ISE will appear, where the attacker can carry out further attacks:

IrfanView
IrfanView is a popular image viewer that supports many extensions through plug-ins created by the community. Unfortunately, even if we were to create our own malicious plugin we will need administrator privileges to be able to paste it into the appropriate directory.
But there is an alternative way to get out of this application. In the settings of IrfanView, we have the ability to define our own editors - indicating the executable file to be the editor. So we can choose PowerShell, for example, and then try to open the image with it. The result will open a window with PowerShell, with an error about the inability to open the file, which we can safely ignore.
Below is a list of steps to make the attack:
In order to exploit vulnerability, it’s required to perform following steps:
1. Upload PNG image to Citrix environment.
2. Go to attached files (e.g. User Management module).

3. Create new attachment and upload PNG image.

4. Double click newly created attachment, after that IrfanView will open that image:

5. Select “P” button to open IrfanView’s settings.

6. Go to “Miscellaneous” tab:

7. Here it is possible to define additional editors (practically executable files), which can then be executed from IrfanView. To execute the code, set the following path that points to PowerShell:


8. Now save the changes by clicking "Ok.
9. Then go to "File" > "Open with external editor" and select PowerShell.

10. After performing the above actions, a window with PowerShell ISE will appear, where the attacker can carry out further attacks.

File explorer
Interestingly, we do not need external office software at all to carry out the attack. All we need is to use the good old File Explorer. All we need to do is to point in the path bar to the executable file we want to run, which can be, for example, PowerShell:
bash
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Sometimes developers will foresee such a case and block us from running powershell, but we still have a few things in store. We can use other versions of CMD or powershell:
bash
C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe
C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell_ise.exe
C:\Windows\System32\cmd.exe
If the above examples are also blocked there is another way. Maybe the administrator has simply blocked the ability to run these tools interactively. But still in the bar with the path we can execute the relevant commands with them, for example:
bash
C:\Windows\System32\cmd.exe /c whoami > C:\whoami.txt
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -command "whoami > C:\\whoami.txt"
Mitigation
First of all, it's worth minimizing the amount of external software available in the application infrastructure. Desktop as a Service machines should have one purpose and that should be to run applications. In addition, you should block access to all tools that are not required for the proper functioning of the application.
Using a network share with weak permissions
Application developers often create such a shared network resource so that each application user has the ability to save changes to their applications and so that these changes are persistent and available on all infrastructure machines.
But it also has an additional use - centralized application configuration management. Administrators can keep an application configuration file on such a share, which contains information about the server's IP address, even some credentials to external services and many more.
This can be a particularly dangerous scenario when the application is vulnerable to DLL Hijacking, Command Injection or other attacks that can be embedded within the file system. The combination of these vulnerabilities, a shared network share and its weak permissions is an explosive mix. The aforementioned vulnerabilities (and more) will be executed within any user that runs the application.
This scenario poses a significant risk as the vulnerabilities can affect any user running the application, potentially compromising multiple instances of machines within the infrastructure. Thus, the combination of weak permissions on shared network resources and various vulnerabilities amplifies the attack surface, making it crucial for organizations to implement robust security measures to protect against such threats.
Summary
The article discusses the emergence of Desktop as a Service (DaaS) applications, which allow users to stream native desktop applications from the cloud to their browser. It highlights how testing these applications requires auditing the entire runtime environment, expanding the attack surface and associated risks. The main vulnerabilities discussed are DLL Hijacking and Command Injection, which can lead to code execution and system compromise. Additionally, it explores exploiting third-party applications like office suites, image viewers, and File Explorer to gain system access. The article emphasizes the importance of implementing robust security measures to mitigate these risks, particularly in scenarios involving shared network resources with weak permissions, which can exacerbate vulnerabilities and compromise multiple machines within an infrastructure.
The use of Desktop as a Service (DaaS) solutions poses significant security risks, including increased attack surface, exploitation of vulnerabilities such as DLL Hijacking and Command Injection, risks associated with third-party applications, vulnerabilities in shared network resources, concerns about data privacy and compliance, dependency on service providers, and challenges in mitigation.
#DaaS #Cybersecurity #Pentesting #RealWorldPentests #PentestChronicles
Next Pentest Chronicles

When Usernames Become Passwords: A Real-World Case Study of Weak Password Practices
Michał WNękowicz
9 June 2023
In today's world, ensuring the security of our accounts is more crucial than ever. Just as keys protect the doors to our homes, passwords serve as the first line of defense for our data and assets. It's easy to assume that technical individuals, such as developers and IT professionals, always use strong, unique passwords to keep ...

SOCMINT – or rather OSINT of social media
Tomasz Turba
October 15 2022
SOCMINT is the process of gathering and analyzing the information collected from various social networks, channels and communication groups in order to track down an object, gather as much partial data as possible, and potentially to understand its operation. All this in order to analyze the collected information and to achieve that goal by making …

PyScript – or rather Python in your browser + what can be done with it?
michał bentkowski
10 september 2022
PyScript – or rather Python in your browser + what can be done with it? A few days ago, the Anaconda project announced the PyScript framework, which allows Python code to be executed directly in the browser. Additionally, it also covers its integration with HTML and JS code. An execution of the Python code in …


